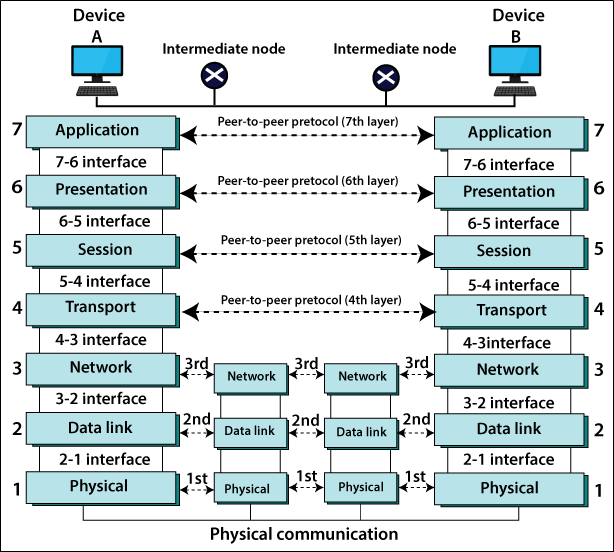
Network layer is responsible for the source to desitnation delivery of a packet across multiple networks.

Routing is process/method to design a routing table. Switching is a method to send the data to the destination/next router.
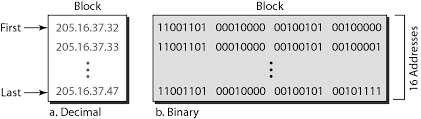
Each host and router on the Internet is assigned a unique 32-bit logical address known as IP address.
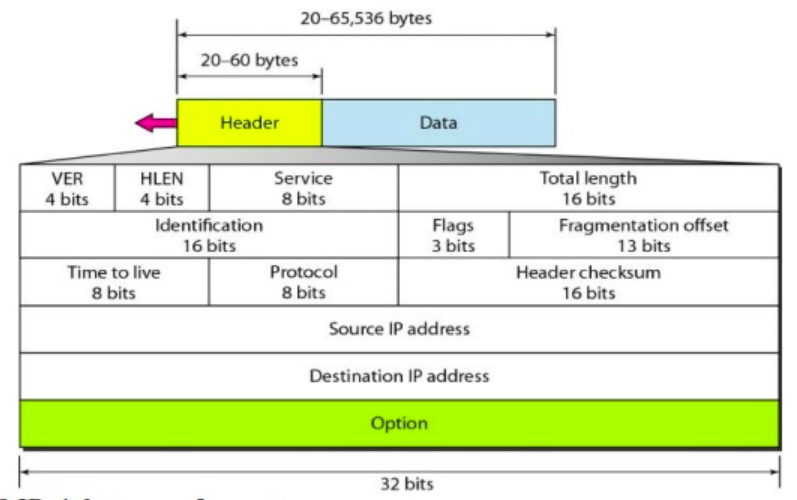
IPv4 addresses are fundamental for identifying devices in a network. Key aspects include:
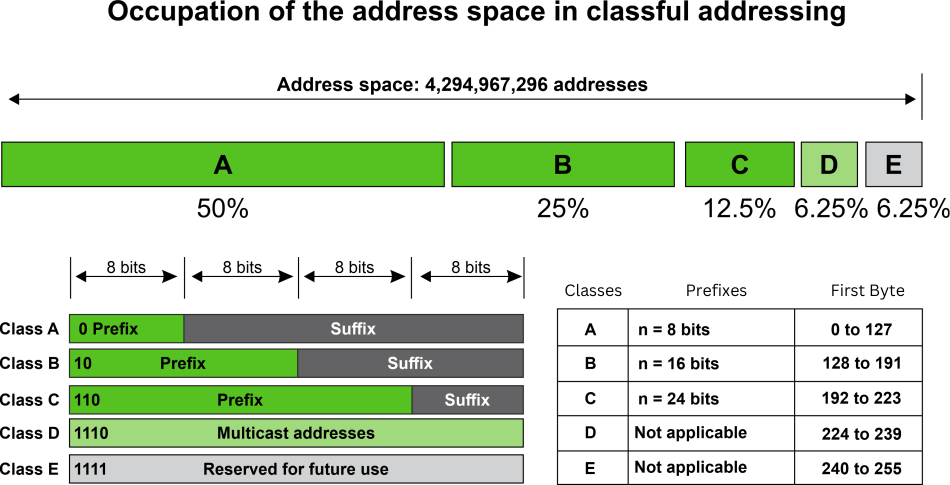
IP addressing supports five different address classes : A, B, C, D and E. Only classes A, B and C are available for commercial use.
Subnetting is a process of dividing an IP network into smaller networks. Each of these subnets has its own specific address.
Subnetting works by dividing an IP address into two parts: the network address and the host address. The network address identifies the network itself, while the host address identifies a specific device (or “host”) within that network.
Subnetting further divides the host portion of the IP address into smaller units, which can then be assigned to various devices within the network. This is done using a technique called the subnet mask.
The subnet mask is a 32-bit number that separates the network address from the host address. In the subnet mask, bits that correspond to the network address are set to 1, and bits that correspond to the host address are set to 0.
A subnet adderss is created by borrowing bits from the host field and designating them as subnet field.
Advantages : It improves the security and the maintenance and administration is easy.
Limitations : Identification of station is difficult and not possible to directed broadcast from outside network.
Subnet masking is the process of using a subnet mask to divide a large network into smaller networks, called subnets. The subnet mask is a 32-bit number that is used to identify the network and host portions of an IP address.
The subnet mask is a bitmask that is used to extract the network and host portions of an IP address. The first n bits of the subnet mask are set to 1, where n is the number of bits used for the network portion of the address. The remaining bits are set to 0.
For example, a subnet mask of 255.255.255.0 has 24 bits set to 1, which means that the first 24 bits of the IP address are used for the network portion and the last 8 bits are used for the host portion. The subnet mask is used by routers to determine which network a packet belongs to. When a router receives a packet, it compares the destination IP address of the packet to the subnet masks of all of the networks that it is connected to. If the destination IP address matches the subnet mask of one of the networks, the router forwards the packet to that network. If the destination IP address does not match any of the subnet masks, the router drops the packet.Subnet masking is a fundamental concept in IP networking. It is used to improve the efficiency of IP addressing, to improve network security, and to make it easier to manage networks.
To overcome the problem of address depletion and give more organization acccess to internet, classless addressing was designed and implemented.
When an entity, small or large, needs to be connevted to Internet, it is granted a block or range of addresses. The size of the block (the number of addresses) varies based on the nature and size of the entity. For e.g. a household may be given only 2 addresses, a large organization may be given thousands of addresses.
To simplify the handling of addresses, the Internet authorities impose three restrictions on classless address block :
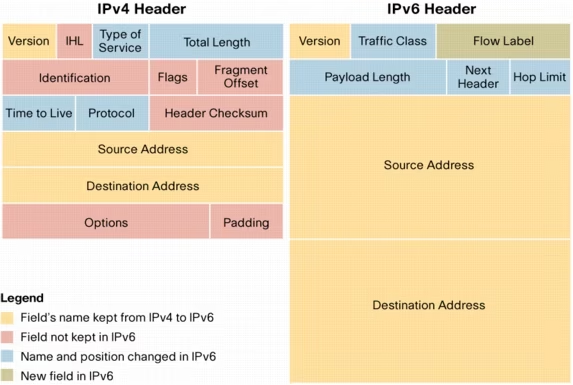
IPv6 addresses aim to overcome the limitations of IPv4.
IPV6 is also known as IPng (Internetworking Protocol, next generation).
Key features include :
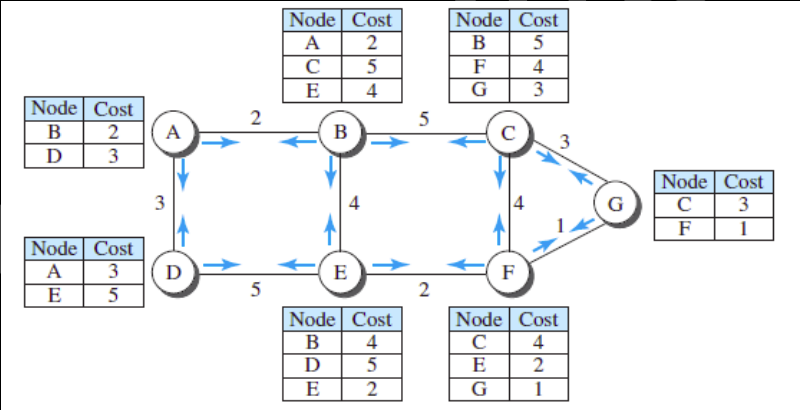
Routing algorithms are essential for determining the most efficient paths for data transmission.
A routing alogrithm should possess some desirable properties like correctness, simplicity, robustness, stability, fairness and optimality.
In static routing, predetermined paths are configured manually. While simple, it lacks adaptability to dynamic network changes.
Dynamic routing employs algorithms that adjust to changing network conditions, optimizing data flow dynamically.
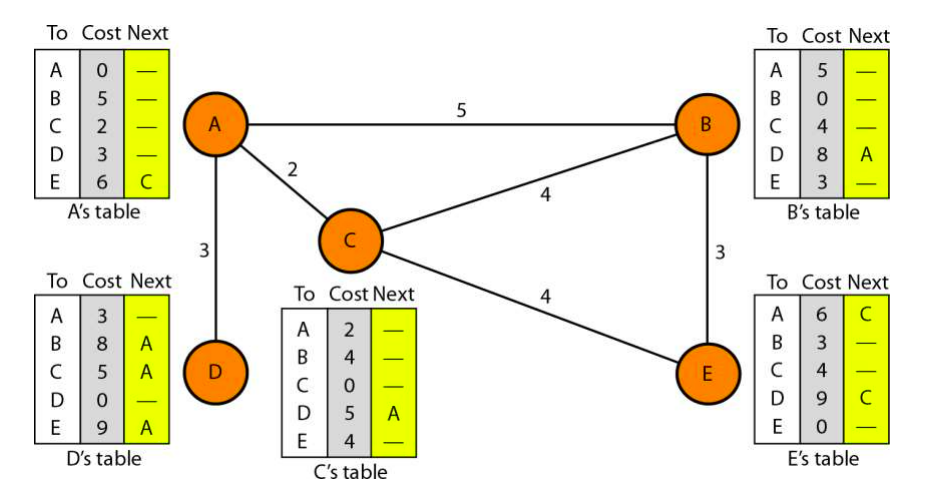
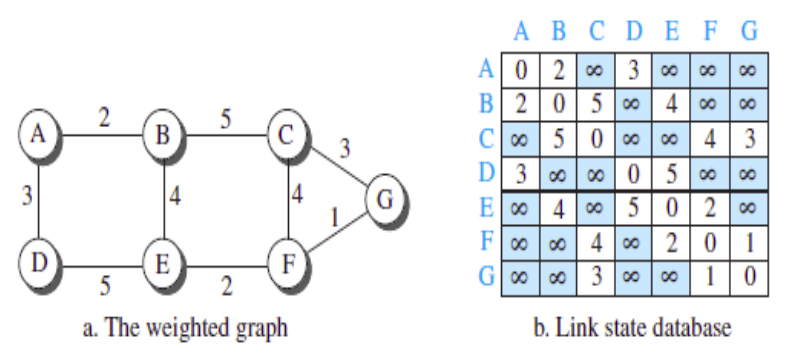
| Criteria | Distance Vector Routing | Link State Routing |
|---|---|---|
| Information Exchange | Periodic sharing of routing tables with neighbors. | Sharing information about neighbors with all routers by broadcasting. |
| Routing Decision | Based on the accumulated distance or cost to reach each destination. | Builds a comprehensive map of the network and determines optimal routes based on this information. |
| Message Overhead | Higher due to periodic updates and sharing with neighbors. | Lower due to broadcasting messages only when there are changes in the network. |
| Network Map | Routers have a limited view of the network. | Each router has a complete map of the network. |
IGMP is a group management protocol that mainly manages the group membership in a multicast network.
The multicast routers which are used to route packets to all the members of a particular group use the information from IFMP to determine which hosts are having membership of which group.
A multicast router generally receives thousands of multicast packets that have to be transimitted to various groups. If a router has no knowledge about the group membership, it will broadcast packet and this will increase the load on the network.
In order to save the network from such a problem, a list of groups is maintained when members of the group are present in netwrok. Thus, IGMP helps the multicast router to create and update this list.
This protocol uses three different messages : query message, membership report and leave report.
RPF is a process for Distance Vector Multicast Routing Protocol (DVMRP) algorithms.
In this strategy, the router only forwards those packets that have traveled the shortest path from source to destination. To achieve this, the router pretends that it has a packet to send to the source. In this way, the shortest path to the sender is computed. If the same router is followed by the received packet then it will be forwarded to the next router, otherwise it will be discarded.
RPB is a process for Link State Multicast Routing Protocol (LSMRP) algorithms.
RPF guarantees that each network receives a copy of the multicast packet without the formation of loops. However, RPF does not guarantee that each network receives only one copy , a network may receive two or more copies. The reason is that RPF is not based on the destination address (a group address) , and forwarding is based on the source address.
To solve this problem, RPB is used in which one parent router is defined for each network. The network could accept the mulitcast packets from this parent router only. This router sends packets to those ports for which it is designated as parent. RPB further guarantees that the packet reaches every network and that every network receives only one copy.
The designated parent router can be a router with the shortest path to the source. Because routers periodically send updating packets to each other (in RIP), they can easily determine which router in the neighborhood has the shortest path to the source (when interpreting the source as the destination). If more than one router qualifies, then the router with the smallest IP address is selected.
RPM is a process for RIP algorithms.
RPB does not multicast the packet, it broadcasts it. This is not efficient.
To increase the efficiency, the multicast packet must reach only those networks that have active members for that particular group. This is called reverse path multicasting (RPM). To convert the broadcasting to multicasting , the protocol uses two procedures, pruning and grafting. This is a type of multicasting technique
If a router receives prune message from all the downstram routers, it in turn, sends a prune message to its upstream router.
Broadcasting plays a vital role in network communication. Different types of broadcasting include:
Congestion is a situation in which the performance of network is degraded due to the presence of too many packates in the subnet or when the load on the network is greater than the capacity of the network.
Congestion control mechanisms are divided into two categories:
In this method, policies are used to prevent the congestion before it happens.
Various methods are :
Closed loop congestion control mechanisms try to remove the congestion after it happens.
Various methods are :
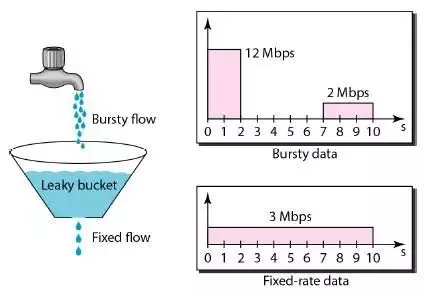
The leaky bucket algorithm is a congestion control algorithm used in computer networks. It is designed to control the rate at which data is transmitted from a source to a destination. The algorithm works by imagining a leaky bucket that can hold a certain amount of data. As data is added to the bucket, it leaks out at a constant rate. If the bucket overflows, the excess data is discarded. This helps regulate the flow of data and prevent congestion in the network.
Implementation : Each host is connected to the netwrok by an interface containing a leaky bucket which is implemented by using a queue that holds the packet. If the queue is full and a new packet arrives, it is discarded. The algorithm uses a clock tick to remove packets from the queue. If the traffic consists of fixed-size packets, a fixed number of packets are removed at each tick. If the packet sizes vary, a fixed number of bytes are removed at each tick. This helps regulate the flow of data and prevent network congestion.
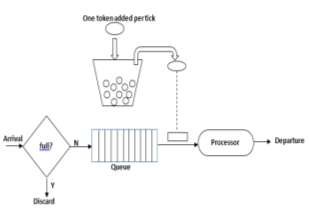
The token bucket algorithm is another congestion control algorithm used in computer networks. It is designed to control the rate at which data is transmitted by using tokens. The algorithm works by imagining a bucket that holds tokens. Each token represents a fixed amount of data. As data is transmitted, tokens are consumed from the bucket. If the bucket is empty, no more data can be transmitted until new tokens are added. This helps regulate the flow of data and prevent congestion in the network.
Implementation : The token bucket is implemented by using a counter that keeps track of the available tokens. When data needs to be transmitted, the algorithm checks if there are enough tokens in the bucket. If there are, the tokens are consumed and the data is transmitted. If there are not enough tokens, the data transmission is delayed until new tokens are added to the bucket. This helps regulate the data transmission rate and prevent network congestion.
Various connecting devices play distinct roles in network architecture:
To prevent confidential information from leaking out and to prevent the entry of virus and other pests, firewalls are used. Firewalls are designed to filter teh packets before passing the traffic outside and all incoming packets destined for a specific host or a server.
It consists two components : Two routers (packet filters) and application gateway.
A packet-filter firewall is a firewall that filters packets based on the destination IP address. It is used to forward or block packets on the basis of nmber of factors such as source and destination IP address, port number, type of protocol.
It maintainsa filtering table that decides which packets are to be forwared or discarded. It filters at network or transport layer.
Proxy firewall operates at application layer. It is used when we want to filter a message on the basis of information contained in message itself.